The “CryptoLocker” virus has been making a great deal of noise lately. 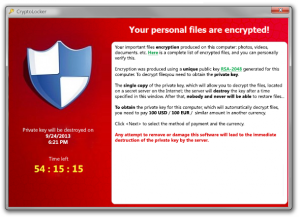 Though we at Thom Infotech have not personally encountered it, we know others who have. We’ve written this post to help you to understand and defend against the CryptoLocker virus.
Though we at Thom Infotech have not personally encountered it, we know others who have. We’ve written this post to help you to understand and defend against the CryptoLocker virus.
What is it?
CryptoLocker is an insidious twist on the all-too-familiar virus or malware infection. “Ransomware” would more accurately describe the threat since the author seeks to extort money from his (or her) victims. Here’s how it works.
CryptoLocker is delivered in the same way most virus and malware infections have been delivered in recent years. The typical infection starts with a cleverly-worded email message containing an attachment. The attachment, once opened, installs a malicious program on your computer. The newly-installed program subsequently scours your hard drive for important files. Not only that, it also searches attached hard drives, flash drives, and any accessible network resources it can find. It then locks your important files using strong encryption protocols that, in effect, make your files inaccessible. Shortly thereafter a message is displayed on your computer screen similar to the one pictured. This is often your first clue something is amiss.The message informs you that you must pay a ransom to regain access to your files. This is no joke – the virus writer is serious and the scheme appears to be working.
Your antivirus software cannot restore access to your files. In many cases your software doesn’t even detect the infection. This is because the virus is “polymorphic” (from the Greek words “polu” meaning “many” and “morphe” meaning “transform”). This means the virus automatically undergoes many transformations in an effort to thwart signature-based antivirus software. Regardless, detecting or cleaning the virus makes no difference to the encrypted files. The damage has been done and you are left with a choice – pay up (not recommended) or kiss your files goodbye. Forever.
What can you do?
Well that’s easy. Just clean the virus and restore the damaged files from your data backup solution. You’ll be back in business in no time. This is, of course, assuming you have data backups. What? No backups? Then you really are out of luck (or out roughly $300 – the cost of the decryption key).
How can you defend against the CryptoLocker virus?
An ounce of prevention is worth a pound of cure (at least that’s what Grandma used to say when she had her teeth in). This is, after all, just a virus. There’s nothing new here except the brazenness and effectiveness of the scheme. Here are our recommendations:
- Deploy a quality managed backup solution – It’s shocking how few people back up their computers. Businesses need to assess the potential impact of a catastrophic data loss event regardless of cause. Imagine one of your users clicking the payload. Their computer is infected, their files are locked, and so are all of the important files on your server’s shared volumes. You can guard against this by making certain your server is being backed up on a regular basis and that the backup files are inaccessible to the end users (lest they also become encrypted). The RescueSMB solutions offered by Thom Infotech will do this, while taking the additional step of replicating the backup files to a secure offsite data center. What about the computers? That’s a bit more difficult. In a perfect world, users will not store critical files on their computers. In the real world, users will store critical files on their computers. Thom Infotech recommends that you identify computers containing this information and back them up too. We have excellent managed PC backup solutions in our RescueSMB offering. In either case, we configure, monitor, maintain, and test the backup solution on a regular basis to give our clients peace of mind regarding the accessibility of their critical information assets.
- Deploy a quality managed antivirus solution. – If you’re a Thom Infotech client you are already protected. Our antivirus solutions are second to none and we monitor them around the clock. Though we’re confident of our solutions, you need to understand that antivirus software alone is not enough. As mentioned earlier, this virus (and others like it) will undergo thousands of transformations. Even the best antivirus software will be fooled by polymorphic viruses.
- Deploy a quality managed email security solution – Since this virus appears to be spreading through email attachments, we recommend that our clients use an external cloud-based email security solution to examine and filter messages as they arrive. Our hosted email security solution is second to none. Nevertheless, 100% detection is not possible with polymorphic viruses.
- Deploy a quality managed Unified Threat Management (UTM) firewall – All traffic entering and leaving your network should flow through a UTM firewall. Nearly everyone has a firewall, but the UTM firewall is unfortunately less common. This class of firewall leverages subscription-based protection to examine all traffic that passes through the device. Detected threats can often be thwarted before they enter your network. Additionally, we can be alerted when suspicious traffic is detected. Furthermore, a quality UTM firewall provides web content filtering to block access to undesirable and dangerous websites.
- Deploy a managed software patch maintenance solution – Viruses like CryptoLocker often gain a foothold by exploiting flaws in unpatched software. This is especially true of “drive-by” attacks that occur when users are tricked into visiting infected websites. Our clients are protected via our TotalCare vulnerability assessment and patch management platform. Patches to the operating system and popular third-party programs such as those from Adobe and Oracle (Java) are handled automatically as part of our TotalCare managed Services solution.
- Educate yourself – Reading this blog post is an excellent start. You are now vastly more informed than most. Trust your instincts when you receive an email that seems a little “off”. It’s always better to confirm it with a professional than to tempt fate and open the attachment. Practice safe internet use. Stop goofing off – many viruses are spread via social engineering which targets careless users as they Google the latest trendy topic. Create and enforce policies that prohibit the personal use of company computers. In particular, configure the UTM firewall to block access to Facebook and popular personal email websites such as Gmail, Hotmail, Yahoo, Comcast, etc. Many infections bypass your countermeasures in this way.
As you can see, many steps are necessary to defend against the CryptoLocker virus. A multi-pronged strategy using multiple tools can greatly reduce your “threat surface” (or points of weakness). Above all, be sure to hire a qualified security and backup vendor to monitor, manage, and secure your network.
